Stave 'Cyber Manager'
Transforming Your Cybersecurity Approach on ServiceNow
Your Zero Trust Security Solution
on ServiceNow
In an era where cyber threats are increasingly sophisticated and pervasive, traditional security measures no longer suffice. Stave’s Cybersecurity Manager offers a robust solution designed to protect your organization through a Zero Trust security model.
Stave’s Cybermanager’s approach ensures rigorous verification of all access requests, maintaining the principle that trust is never assumed, regardless of the requester’s location.
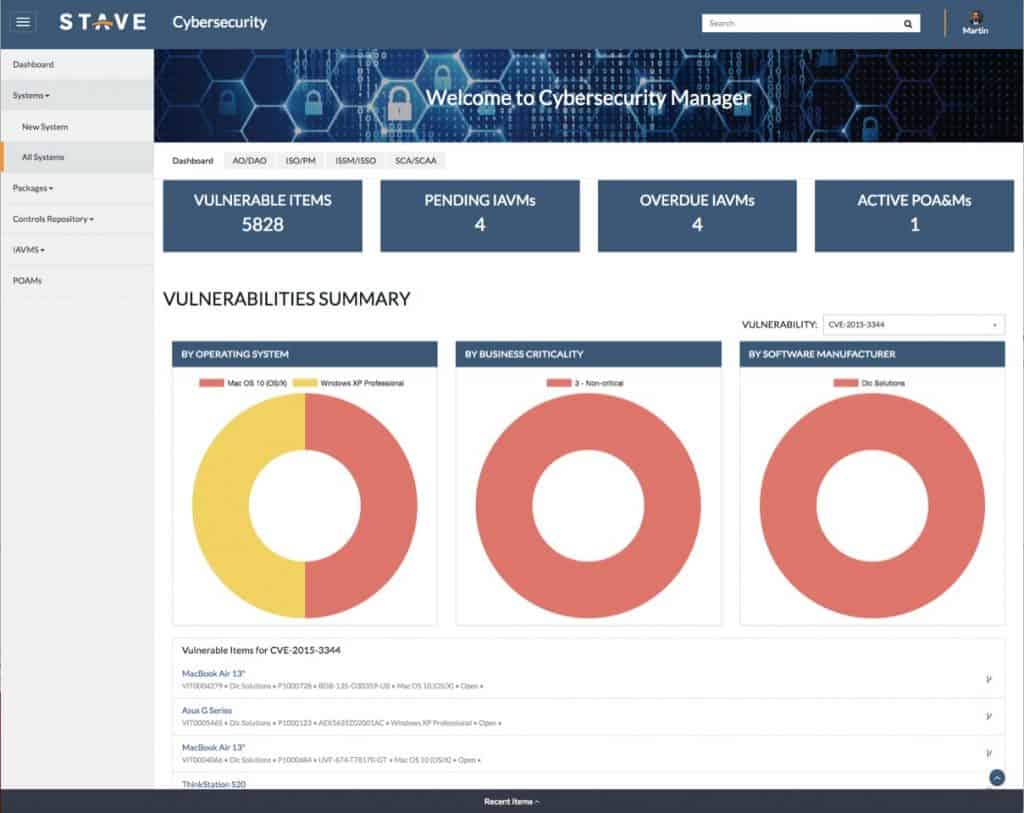
Elevating Your Security Posture on ServiceNow
Embrace a future where your organization is safeguarded by a Zero Trust framework with Stave’s Cybersecurity Manager. Our solution offers a streamlined, effective path to robust cybersecurity, ensuring your assets are protected and your compliance needs are met with ease.
Customer Feedback:
The Comprehensive Impact of Stave’s Cybersecurity Manager on ServiceNow
How: Enhances protection against financial fraud and cyberattacks, ensures compliance with stringent regulatory requirements, and secures sensitive customer data.
How: Safeguards customer data and financial transactions, supports PCI DSS compliance, and helps prevent data breaches that could erode customer trust.
How: Secures critical infrastructure, supports compliance with industry regulations like NERC CIP, and protects against threats to operational technology (OT) systems.
How: Protects against disruptions to supply chains, secures customer and operational data, and supports the integrity and availability of logistics systems.
How: Protects patient data in compliance with HIPAA and other regulations, secures healthcare IT infrastructure, and supports the confidentiality, integrity, and availability of critical health information systems.
How: Protects intellectual property and sensitive data, secures industrial control systems against cyber-physical threats, and supports the integrity of supply chains.
How: Protects intellectual property and customer data, supports secure software development practices, and ensures the integrity of cloud services and data centers.
How: Protects intellectual property and customer data, supports secure software development practices, and ensures the integrity of cloud services and data centers.
How: Secures sensitive government data, supports compliance with federal cybersecurity mandates, and protects infrastructure from nation-state and insider threats.
How: Secures student and faculty data, protects research data, and ensures safe digital learning environments against cyber threats and data breaches.
How: Secures network infrastructure, protects customer data, and ensures the resilience of communication services against cyberattacks and disruptions.
How: Protects guest information, secures booking systems, and maintains operational integrity against cyber threats.
Beyond Defense: Transformative Cybersecurity with Stave’s Solution
Benefit from continuous monitoring and adaptive responses to emerging threats, keeping your organization one step ahead of potential security breaches.
Leverage a solution designed from the ground up to embody the principle of “never trust, always verify,” ensuring comprehensive security across your digital landscape.
Streamline your path to compliance with automated workflows, significantly reducing manual effort and accelerating the remediation process.
With a solution that grows with your needs, Stave’s Cybersecurity Manager offers flexibility and scalability, ensuring your security posture strengthens in tandem with your organization.

NIST Compliance
Cybersecurity Manager transforms the daunting NIST SP 800-37 Risk Management Framework (RMF) process into a streamlined, effortless journey towards compliance. By harnessing the power of automation, it not only simplifies each step of the RMF but also catapults organizations ahead in their compliance journey, minimizing manual labor and maximizing efficiency. With Cybersecurity Manager, navigating through the complexities of categorizing information systems, selecting and implementing security controls, and ensuring continuous monitoring becomes a seamless experience. This innovative solution empowers organizations to not just meet but exceed NIST standards, fortifying their cybersecurity defenses and securing their digital assets with unparalleled ease and precision. Embrace the future of compliance with Cybersecurity Manager, where meeting NIST standards is not just simple—it’s a strategic advantage.
The StandardizedPro Advantage on ServiceNow
Beyond Defense: Transformative Cybersecurity with Stave’s Solution

- Automated scanning of network to identify all connected devices and software.
- Classification of assets based on type, criticality, and compliance requirements.
- Centralized repository for all asset data.
- Real-time updates to asset status and attributes.
- Mapping of assets to relevant compliance frameworks (e.g., NIST, HIPAA, GDPR).
- Automated compliance status monitoring for each asset.
- Identification and cataloging of vulnerabilities affecting assets.
- Prioritization of vulnerabilities based on risk assessment.
- Generation of automated remediation tasks for non-compliant or vulnerable assets.
- Tracking of remediation progress and status updates.
- Application of security policies based on asset classification and compliance requirements.
- Dynamic adjustment of policies in response to changes in asset status or threat landscape.
- Continuous assessment of risks associated with each asset.
- Generation of risk scores and prioritization of risk mitigation efforts.
- Customizable reports on asset inventory, compliance status, vulnerabilities, and remediation efforts.
- Dashboards providing at-a-glance insights into the overall security posture.
- Seamless sharing of asset and security data with Cybersecurity Manager for coordinated threat response.
- Integration with other security tools and platforms for comprehensive data analysis.
- 24/7 monitoring of assets for changes in status, new vulnerabilities, or compliance drift.
- Alerts and notifications for significant events or incidents requiring attention.
The integration of Cybersecurity Manager and StandardizedPro into a Zero Trust framework, as described, offers a distinctive approach to implementing Zero Trust security principles. To understand how this differs from other Zero Trust solutions, it’s essential to consider the unique aspects of their collaboration, the depth of integration, and the focus on asset management as a cornerstone of security. Here’s a detailed comparison:
The deep integration between asset management (StandardizedPro) and security management (Cybersecurity Manager) is a standout feature. While many Zero Trust solutions emphasize network segmentation, identity verification, and access control, the combination of Cybersecurity Manager and StandardizedPro places a significant emphasis on asset intelligence as the foundation of security decisions. This ensures that security policies and access controls are dynamically applied based on the most current understanding of each asset’s context, including its security posture, compliance status, and operational role.
Other solutions might treat asset management as a separate or secondary concern, not fully integrated into the real-time decision-making processes of their Zero Trust architecture. By contrast, this integrated approach ensures that every decision is informed by detailed, up-to-date asset data, enhancing the precision of security controls and the effectiveness of threat detection and response.
The synergy between Cybersecurity Manager and StandardizedPro facilitates dynamic policy enforcement and automated remediation workflows that are directly tied to asset status and compliance. This means that security policies are not static but evolve as the asset landscape changes, ensuring that the organization’s security posture is always aligned with its current risk profile.
While many Zero Trust frameworks include dynamic policy enforcement, the level of automation and integration with asset management provided here allows for a more seamless and automated transition between detection, decision-making, and action. Other solutions may require more manual intervention to update policies based on changing asset information or to initiate remediation actions.
The described integration is designed to be inherently scalable and flexible, accommodating the growth of an organization’s asset inventory and the evolution of its security needs without requiring a fundamental overhaul of the security infrastructure. This is particularly important in environments that are rapidly changing or expanding, such as those adopting cloud services, IoT devices, and remote work models.
Some Zero Trust solutions may be more rigid or modular, requiring significant adjustments or additional modules to scale up or adapt to new types of assets and threats. The described approach, by contrast, is built to adapt and scale more fluidly, potentially offering a lower total cost of ownership and a more straightforward path to expanding or adjusting the security framework.
The real-time data exchange and coordinated actions between Cybersecurity Manager and StandardizedPro enable an exceptionally responsive security posture. This integration allows for immediate adjustments to access controls and security policies in response to new threats, vulnerabilities, or changes in asset status.
While real-time response is a goal of many Zero Trust solutions, the effectiveness of this response can be limited by the quality and timeliness of the data informing it. The direct integration of asset management and security management here ensures that responses are based on comprehensive and current data, enhancing the speed and accuracy of the security response.
Emphasizing the entire lifecycle of assets, from procurement to decommissioning, ensures that security is a continuous consideration, not just at the point of access or during active use. This lifecycle approach to asset management within a Zero Trust framework ensures that assets are always accounted for and evaluated for risk, even as they move, change, or leave the network.
Other Zero Trust frameworks may focus more on the point of access or the active phase of an asset’s lifecycle, potentially overlooking the security implications of assets that are being moved, repurposed, or retired. The integrated approach ensures a holistic view of security that encompasses the entire asset lifecycle.